With the proliferation of advanced driver assistance systems (ADAS) among the fleet, the hardening of the vehicle networks and modules is front and center for many vehicle manufacturers. Today, technicians are already facing challenges when interfacing late-model vehicle systems. This article will help you prepare for these security-laden vehicles, which will help smooth out future service and repair operations for you and your shop.
As we entered the 21st century, the automobile was beginning to become more complex due to the implementation of additional micro-controllers. Near the end of that first decade, the automobile was beginning to experience a technology shift with the addition of driver assistance features. At that time, we were beginning to see vehicles running on approximately 50 million lines of code. Today, it is not uncommon to see vehicles running on more than 150 million lines of code. What’s driving all this technology? There are three primary drivers:
1. Safety
2. Emissions/fuel economy
3. Driver convenience
As manufacturers continued to develop and refine systems to enhance the vehicle, the focus on various facets of vehicle security wasn’t given high priority. Today’s vehicles contain numerous attack vectors that are rarely discussed. Keyless entry, TPMS, cellular data, telematics, and the OBD-II diagnostic connector are all present vulnerabilities.
Since 2008, manufacturers have been required to equip their vehicles with controller area network(s) (CAN). Since that time, various systems have had the means to share information freely and openly. When one connects a device to the OBD-II port, the potential for malicious activity is very real.
In 2015, two white-hat hackers, Charlie Miller and Chris Valasek, demonstrated such vulnerabilities on a 2014 Jeep Cherokee. The two proved that security flaws weren’t limited to the vehicle manufacturer as it also included the cellular network providers supporting Fiat Chrysler Automobile’s (FCA) Uconnect telematics system.
Their work sparked a major reprioritization of security at the highest levels, and this is one of the reasons we’re now seeing different security features being introduced into the vehicle. Additionally, there will likely be federal regulations in place sometime in the future.
FCA (Now Stellantis)
Since 2018, FCA began producing vehicles with a new Secure Gateway Module (SGM) (Figure 1). What this did was remove direct scan tool access from the J1962 OBD-II connector for any of the networked modules not related to OBD-II emissions. Sometime after SGM’s introduction, a solution was born. Today, many of the aftermarket scan tools have established licenses with the AutoAuth program in order for their customers to obtain access to systems behind the SGM. Right now, the following tool manufacturers offer tools that will allow for secure access under this agreement:
- Autel
- Bartec
- Belron
- Bosch
- CAS
- Hunter Engineering Company
- Launch Tech USA
- Mac Tools
- Matco Tools
- Mitchell 1
- Opus IVS
- OTC
- Safelite
- Service Lane eAdvisor
- Snap-on
- TOPDON
If a service provider wants to gain access to FCA’s systems that reside behind the SGM, they will need to register their shop with AutoAuth. From there, the shop is allocated six user slots under the $50/yr license. AutoAuth provides a plan that costs $2/user/year if additional users are needed Once the shop is registered, they can then begin to add supported tools under their AutoAuth account. To begin tool registration, one will need each tool’s serial number to complete the process. Once all that is in place, registered users will be able to access all modules on FCA’s SGM-equipped vehicles.
Ford
Since around 2019, Ford established security for some of the ADAS systems on their vehicles. Even with the Ford Diagnostic and Repair System (FDRS) and Ford J2534 Diagnostic Software (FJDS), aftermarket users cannot access these systems without the use of a valid Vehicle Security Professional (VSP) credential issued by the National Automotive Service Task Force (NASTF).
NASTF
NASTF’s Vehicle Security Professional (VSP) program is essentially a trust system that is used to establish authentic operations into various vehicle security-related functions. There are multiple entities that make up this trust system, which includes OEMs, the National Insurance Crime Bureau (NICB), and the NASTF Registry. If you’re interested in gaining authentic access to security-related operations, then you’ll want to apply for an account with NASTF.
To start, you’ll need to become a member of NASTF, which you can do for free. Then, you’ll want to log into your NASTF account and look for the “Vehicle Security” link. On that page you’ll find a ton of information including a checklist that will help you get started. There is an application fee that covers many things including a background check. NASTF reports that if an application is submitted with everything required, the approval process can take as little as a few days. However, I recommend that you try and obtain your credentials in advance of you actually needing them. If you’re using OEM websites for service operations, you’ll want to look for any areas that discuss NASTF and be sure to get your NASTF VSP ID connected to the OEM sites you use.
Ultimately, this will help you move related security operations through the shop more efficiently. Nowadays, almost everything we touch is security related, so you’ll want to raise your awareness of the requirements needed so that the road blocks you experience are minimized.
Operations
In the future, there may be additional requirements for your service center to meet in order to be able to access security-related operations. Things such as in-house firewalls, malware/spyware/virus detection software, and more may be items you might want to think about. In fact, most businesses would benefit from performing a security check of their internal operations so that they can be sure that their cyber-security practices are not putting the company in jeopardy.
Other vehicle manufacturers
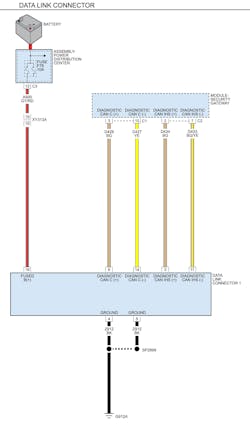
Who else will be moving their platforms in the secure gateway direction? According to the Equipment and Tool Institute (ETI), they reported during the February 2021 Town Hall that Nissan’s 2020 Sentra is now using a secure gateway and should have a third -party access program in place for the aftermarket in the very near future. Check out the network communications wiring diagram for the 2020 Sentra and you’ll see a new device called the 8-channel CAN Gateway (Figure 2). While gateways have been populating vehicles for some time now, others like Kia, Hyundai, and Mercedes-Benz will be deploying secure gateways on their vehicles soon. Secure access to vehicle data will indeed become part of our processes. It is best to stay ahead of the curve and stay tuned to this new challenge.