Automotive security: From basic locks to advanced cybersecurity
Automotive security has evolved tremendously over the years. In the beginning, we had simple mechanical locks preventing physical theft. Today’s systems could be characterized as highly sophisticated digital fortresses, encompassing a vast range of technologies from basic alarms to complex electronic and cybersecurity systems with vehicle tracking and more. This evolution not only reflects the advancement in automotive technology but also the changing landscape of vehicle theft and the need to protect and maintain critical vehicle systems.
Vehicle theft reasons – More than you may be aware of
Vehicle theft is supporting more than just the purpose of parts or a free ride. It provides financial support for nefarious activities such as human trafficking, drugs, and more. Many vehicles that are shipped offshore are disassembled for parts, but even those that are not are rarely ever recovered. Many years ago, Mercedes-Benz launched the Theft Relevant Parts (TRP) program which serves to disincentivize thieves from stealing their vehicles for parts or reenabling vehicles that have partially disassembled.
Advanced security systems in modern vehicles
Modern vehicles are equipped with a variety of security systems, and this is where service professionals need to have access to proper service information and tooling. These include electronic immobilizers, which prevent the engine from starting by disabling the fuel, ignition, and or starting systems without the correct key or transponder. Some are equipped with sophisticated systems that include cameras and other sensors that detect movement, glass breakage, and unauthorized entry as well as possess GPS tracking devices that can support vehicle recovery following theft. GPS antennas are typically an area that thieves try to disable by disconnecting critical cabling during theft often damaging harnesses. This is something a technician needs to be aware of when troubleshooting GPS-related faults.
Vehicle camera systems – Providing support for law enforcement
Some vehicle manufacturers can provide support for crime investigations. Today it is not uncommon for law enforcement to quickly survey a crime scene looking for vehicles supporting such technologies. If the vehicle has its "security mode" active, the official can trigger vehicle recording, record the VIN, and then contact the vehicle manufacturer to obtain video recordings (Figure 1).
The emergence of gateway security systems and cybersecurity
As vehicles have become more “cloud” connected and reliant on computer networks, the risk of cyberattacks has naturally increased. Gateway security systems act as firewalls, controlling access to the vehicle's network and protecting critical safety systems such as collision mitigation and other systems supporting lateral and longitudinal control of the vehicle. These systems are crucial for preventing unauthorized access and ensuring vehicle safety. Some vehicle manufacturers have deployed systems that authenticate the user at the vehicle performing service, creating a trail of vehicle access because of the potential for misuse.
FCA (now Stellantis) security challenges and responses
In 2015, two security researchers Chris Valasek and Charlie Miller exposed significant vulnerabilities in Fiat Chrysler Automobiles (FCA) vehicles, demonstrating remote hacking by taking control of a vehicle underway on public roads. In response, FCA issued software updates and recalled affected vehicles, highlighting the industry's need for constant vigilance and adaptation in cybersecurity. This activity paved the way for the AutoAuth program in place today. See my article from 2021 on this subject: VehicleServicePros.com/53095900.
EU rulings against FCA’s secure gateway
Recent rulings by the European Union (EU) against FCA's secure gateway system may have a significant impact on secure gateway access. In the fall of 2023, questions surfaced about the balance between security and accessibility for vehicle servicing. Currently, FCA is authenticating both the end user and the tool being used to access the vehicle systems residing behind the gateway. General Motors (GM) has had a secure gateway for many years now which has mainly gone unnoticed by service personnel. GM decided long ago that they would be able to secure the vehicle with little to no disruption to the technician. Other manufacturers have either recently introduced a gateway or will be implementing such a system soon. The EU rulings will likely have an impact on how manufacturers authenticate access to vehicle systems.
Tools for managing vehicle security
Professional service technicians use various tools to handle vehicle security operations, including diagnostic scanners and software for accessing vehicle systems along with the previously mentioned service information and professional support channels. While these tools are vital for legitimate servicing, there is great concern about tool misuse to support vehicle theft. In fact, some professional service operators have experienced theft of their diagnostic and service tools primarily because of their ability to support vehicle theft. The National Automotive Service Task Force (NASTF) is currently working with some vehicle and tool manufacturers to investigate ways to secure access to these tools and how they access vehicle systems for service.
Recent security vulnerabilities
Some vehicle manufacturers have recently experienced vulnerabilities that allowed unauthorized vehicle access. One example is that a private CAN bus was physically accessed from outside the vehicle where the bad actor injects a message onto the network spoofing the security system to authenticate and authorize vehicle access. As you can see, these vulnerabilities expose weaknesses in automotive security. This raises even more concerns about vehicle safety and security.
Tesla's security systems
It’s safe to say that Tesla is known as a software company first and a vehicle manufacturer second. As a Tesla owner over the past five years, I have witnessed how advanced and evolutionary their vehicle technology is. Their over-the-air (OTA) updates provide a pathway to deliver vehicle improvements, quick deployment of enhanced vehicle operation, and, of course, support service personnel with problem-solving. Adding keys, programming key cards, authorizing mobile devices and key fobs is a simple operation. Tesla has designed the system so that the vehicle owner can easily carry out these tasks (Figure 2).
Recently, Tesla deployed a secure access method through NASTF where a vehicle security professional (VSP) can request secure access to the vehicle through Tesla’s system which requires the vehicle owner to grant access through their account.
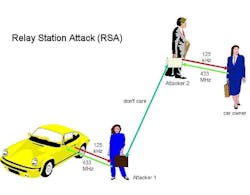
Relay attack vulnerabilities
A relay attack is where a vehicle that doesn’t require a physical key (push button start) is spoofed into thinking that the key fob or authenticated mobile device is near the vehicle. This method typically involves two perps establishing a relay attack station (Figure 3) where one attempts to pick up the key fob signal with an antenna from inside a building or on the person (think shopping at the grocery store) and relay the authentication handshake communication to another person near the vehicle. I’ve seen many videos of this process taking place, and it’s quite perplexing. It makes me think about how these innovative technologies can leave many vehicles vulnerable. Tesla offers an additional layer of security where the owner can set up a PIN to drive. Other manufacturers may offer something similar.
Conclusion
Automotive security is an ever-evolving arena that requires continuous adaptation and advancement. Professional service personnel engaging in automotive service will continue to see more challenges related to security. Service success is highly dependent on the knowledge and skill levels service professionals maintain and the capabilities of their tooling. Consumers will also require updated knowledge and in my opinion, this is where the trusted service professional can build credibility with their clients through education and the demonstration of service professionalism.